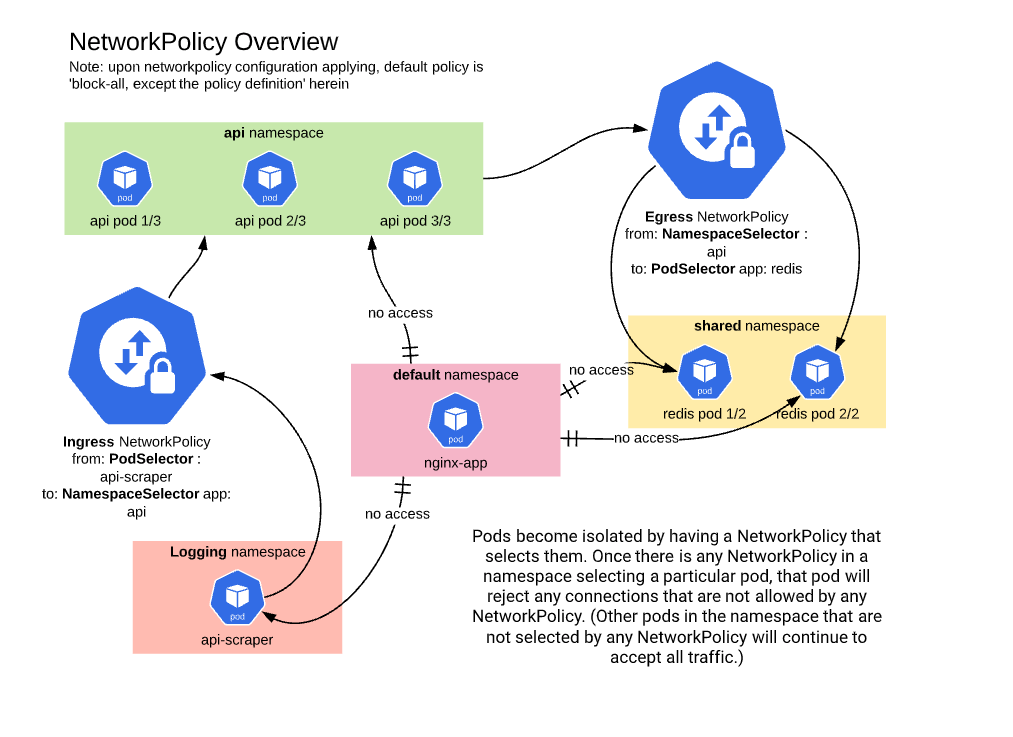
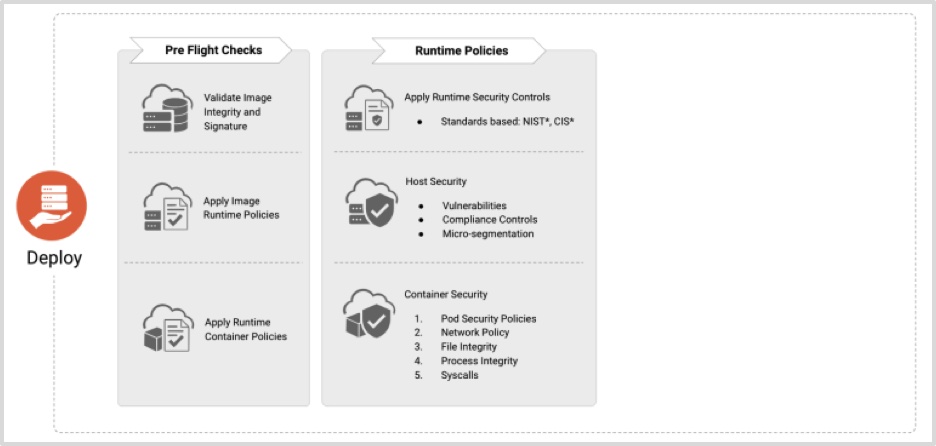
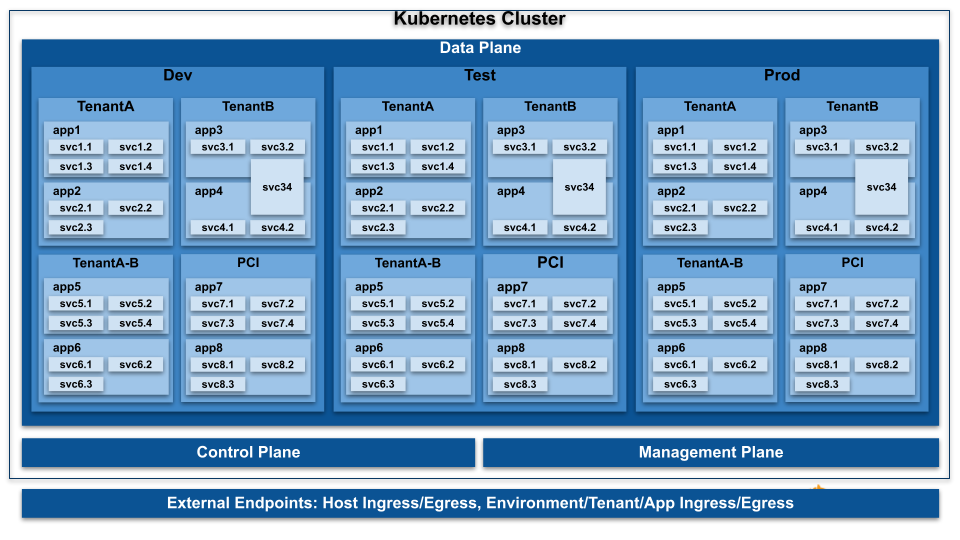
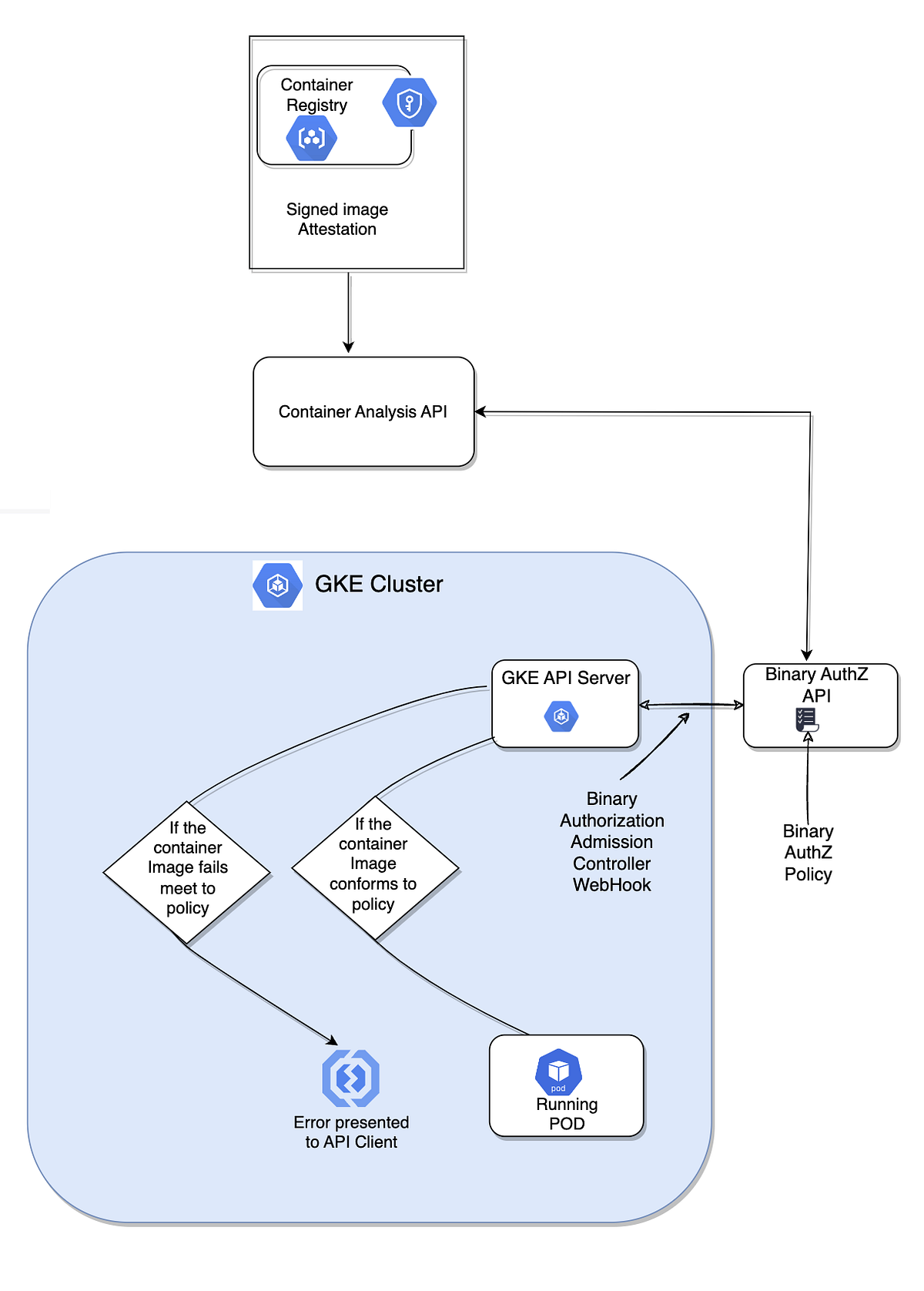
Deep-dive: Kubernetes Network Policy in GKE | by Kishore Jagannath | Google Cloud - Community | Medium

Question: PodSecurityPolicy doesn't allow Pods created by custom MutatingWebhookController that injects sidecar without securityContext.allowPrivilegeEscalation · Issue #65716 · kubernetes/kubernetes · GitHub